Any malicious code that has infected 25,000 computers--60% of them in the United States--and achieved a spam rate of 80 million messages per hour, which in turn lead to 1,400 compromised websites, is a threat worthy of analysis. Such is the case with the malware we detect as Win32/TrojanDownloader.Zortob.B. This computer Trojan can steal credentials and the contents of your mailbox and address book, and is actively spreading itself and other malware, such as Zbot and Medfos--which changes search results in browsers—as well as a FakeAV variant. According to Trend Micro there is another module for Zortob.B that sends Canadian Pharmacy related spam.
Indeed, it was Trend Micro that published a report a few days ago titled “Asprox Reborn” in which researchers provided an in-depth analysis of a piece of malware that ESET refers to as Win32/TrojanDownloader.Zortob.B. The Trend report is quite thorough and we recommend you give it a read. As it turns out we were also in the process of analyzing and tracking this same malware using something called a sinkhole, which we will explain in a moment.
Zortob.B propagates by sending spam that impersonates the IRS and companies such as FedEx, USPS, and American Airlines. You can see an example of one of these spam message below.
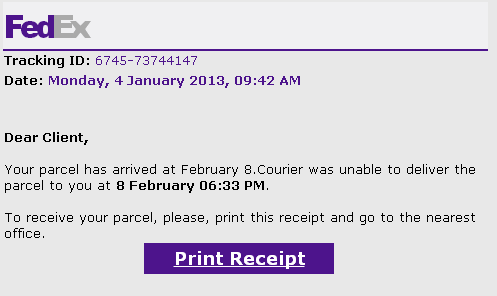
If you follow the instructions in the email, Zortob.B will proceed to infect your computer. The program then installs a spamming module on the infected machine to send more of these messages. In the beginning, the infectious Zortob.B spam messages delivered the malware as an attachment, but since last August we noticed that Zortob.B relies on compromised websites to host the binaries. We have encountered 1,410 such compromised websites in the last seven months. Since mid-February we have observed a clear trend among these websites: The majority of the newly compromised websites appear to be running the popular Wordpress blogging platform.
The people behind Zortob.B employ a number of Command and Control (C&C or C2) machines and these essentially run the operation. While inspecting the list of C&C servers used for the spamming module, we noticed that it was using the domain buybuy41.ru. We also noticed that buybuy41.ru was unregistered. So, on March 4, we registered the domain and pointed it to one of our research servers. This tactic is known as sinkholing because researchers observe the traffic coming in but don’t respond. In other words, they are not participating in the botnet’s malicious activity, simply observing it.
By sinkholing this domain we were able to collect precise information from the computers infected by Zortob.B as they reported to the C&C machine now under our control. For example, when the spamming component connects to a C&C, it sends various information, including a GUID which enables us to uniquely identify the bots. The following figure shows a sample communication attempt from a Zortob.B spamming module.

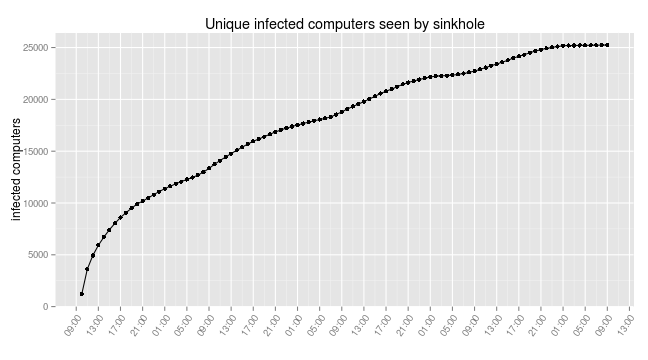
Analyzing the data from our sinkhole we saw that our server was contacted by 25,239 unique bots between March 4 and March 6. By comparison, those same bots contacted us via 32,105 IP addresses, almost 30% more. This discrepancy illustrates the risk of over-estimating the size of a botnet when basing your estimate on the number of IP addresses. It is also worth noting that the spamming component might not be pushed to all the computers infected with Zortob.B (this malware is multi-purpose and in some cases it could just be stealing information and not acting as a spam cannon). The implication is that the real infection count might be higher that what we see just from the spam activity (we should say, however, that when infecting computers in our lab Zortob.B pushed the spamming component every time).
Another factor to take into consideration when assessing the scale of a botnet is the possibility of multiple infected computers behind the same IP address, either because of the use of a dynamic IP pool or the use of NAT, a practice common in Asia due to the limited size of the available IP space for this region. We identified 746 GUIDs for Zortob.B where there were multiple infected computers behind the same IP address, about 2% of the total. Those GUIDs mapped to 493 IP addresses that had as many as 9 GUIDs per IP. All Zortob.B infected computers in Singapore were behind such IP addresses.
Here is a graph of the number of unique Zortob.B infected computers that contacted our sinkholed C&C. The malware contacts one C&C server chosen at random every 7 minutes if it is not busy with a spam job.
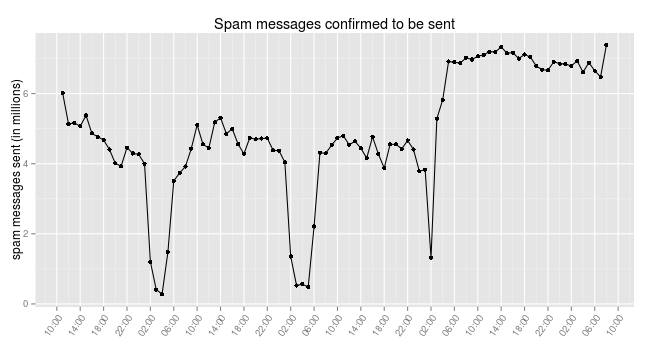
Fortunately, the Zortob.B bots are reporting back to the C&C on the number of spam messages that they have sent. This allows us to estimate the amount of spam sent by the botnet. The following graph shows the number of messages sent every hour, which is around 5 million messages per hour during the day, and went up to 6.5 million messages during the last 24 hours. This is only the number of messages that were reported to our server. As there are 16 C&C servers and the bots only report the information to one of the servers, the hourly spam rate could be as high as 80 million messages per hour or almost 2 billion messages a day.
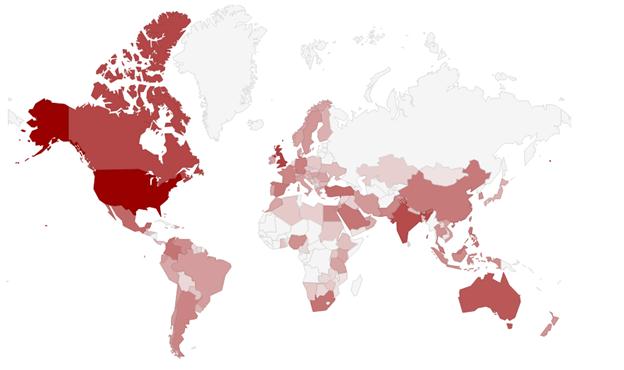
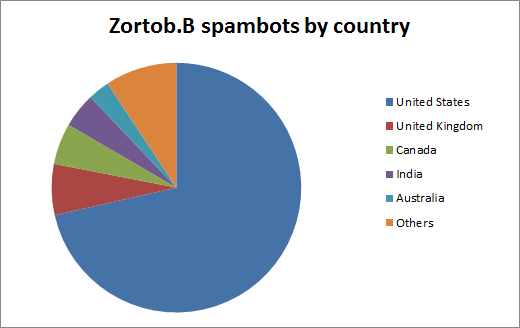
We also had a look at the geographical distribution of the infected computers. The following figure displays the location of Zortob.B infections by country. Note that due to the overwhelming number of bots located in the US, we used a logarithmic scale to make visible the other less infected countries.
More than 60% of the infections are located in the United States. As the spam campaigns target American institutions such as FedEx it is more likely that people from this country would fall for the trick than someone from Japan or France. Our numbers also correspond to those presented by Trend Micro, where they are seeing 75% percent of the spam coming from North America.
The opportunity to have a sinkhole providing us real data on Zortob.B is invaluable. With the number of infections, their geographic distribution and the spamming rate, we clearly see that this is a large and active botnet with a lot of spreading potential. We will continue to monitor this threat and share our findings.
We would like to thank Group-IB for their assistance in this investigation. This analysis was done in collaboration with Olivier Bilodeau, François Chagnon, Alexis Dorais-Joncas, and Pierre-Marc Bureau.