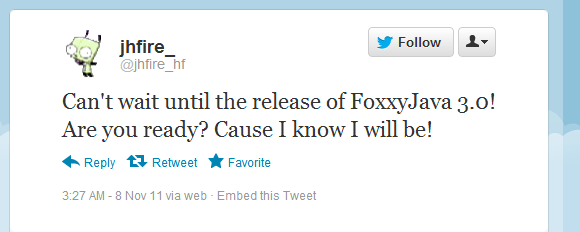Part of my daily routine here at ESET is to inspect URLs for new trends and malware campaigns identified by our systems. A couple of weeks ago I noticed a group of URLs with a similar pattern. When I investigated further, I found out that the URLs pointed to copies of legitimate web sites with a malicious Java applet embedded in them.
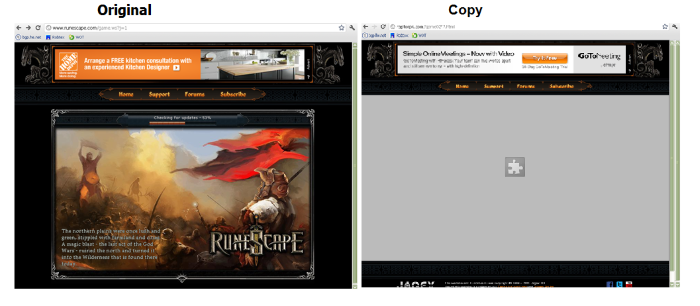
As an example, the following screenshot compares the original web site—in this case, the home page for the popular game RuneScape—side-by-side with its copy. The large gray portion on the copied web site is due to the fact that the Java applet was disabled when the screen shot was taken.
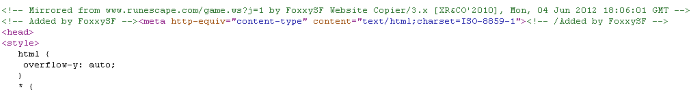
When examining the HTML source code of the copied web sites, I found comments in them stating that the earliest ones had been copied with HTTrack, a popular open-source tool used to save web sites for offline reading. In later instances, the comment had been modified to read FoxxySF Website Copier . It was a bit surprising that the person behind this took the time to modify the comment as opposed to removing it altogether.
A malicious script and Java applet were added to the copied websites. This, in and of itself, is nothing new: Self-signed Java applets have been used for a while now to install malware on computers. Using a copy of the RuneScape website, though, is actually a well-thought-out strategy as the game itself is a Java applet and so users may well be accustomed to seeing Java security dialogs and fall for the trick.
The malicious script was trivially obfuscated and contacted a hit counter hosted on a server at another domain to keep track of the number of visitors to copied web sites.
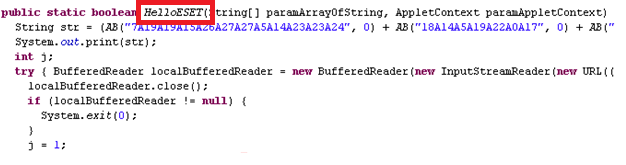
Upon execution, the Java applet would download a malicious executable hosted on various file hosting services and launch it. When decompiling the applet, I found out that the author used HelloESET as the name of a function.
After successfully executing the downloaded file, the applet also performed a callback to the same domain as the script previously mentioned. That domain seemed like an interesting candidate to continue my analysis.
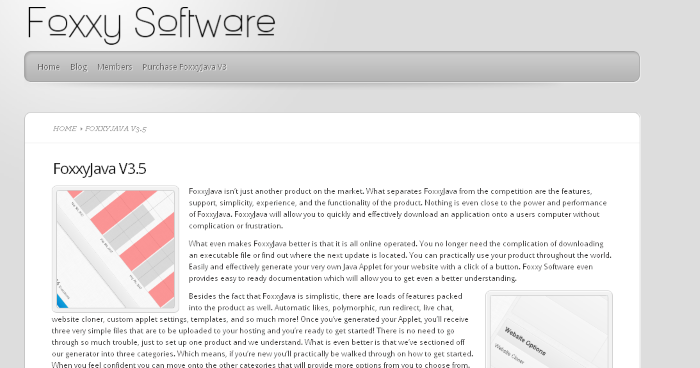
Introducing FoxxySoftware
When visiting the domain in a web browser, I was surprised to discover that it was hosting a website selling access to a malware-distribution service.
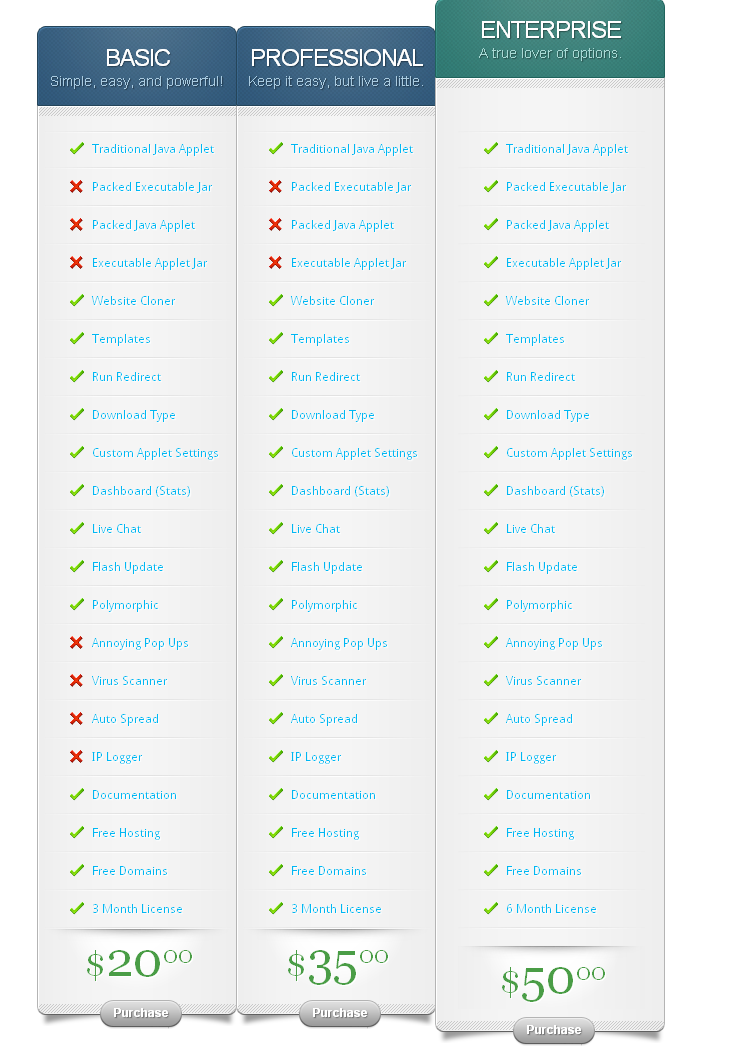
The website contained a comparative of the features in the different versions of the product, mentioning malicious features like website cloner , auto spread , use of packing and scanning with antivirus software to ensure files are not detected prior to distribution. The description even blatantly stated FoxxyJava will allow you to quickly and effectively download an application onto a users computer without complication or frustration .
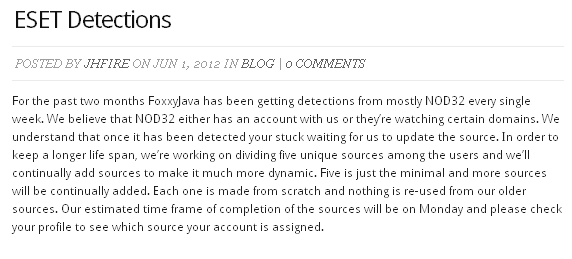
The website even had a blog and in one of the articles the developer complained about detection by our product. The funny thing is that we were not tracking this malware before I started looking into it (which was after he posted his complaint) and we definitely never had an account there.
In addition to the pseudonym used on FoxxySoftware's blog, I also had email addresses and other information gathered from the WHOIS entries for the domain names. My next step was to check and see what additional information I could find linked to these. This is often complicated and time-consuming because malware authors and online miscreants typically take precautions to not leave too much information about themselves behind and to keep their personal life separated from their malevolent persona. Not this time.
Meet JHFIRE
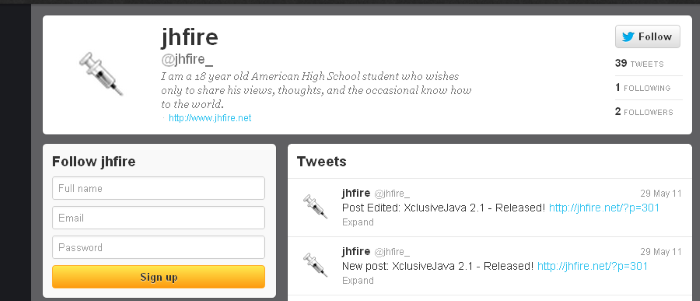
The first things I found were posts on hacking forums where our new friend was advertising his product, which is quite common and not unexpected. I also found older posts using the same pseudonym and style of language where he boasted about using cheats in online games. This is possibly how JHFire started his hacking career. Looking around further, I discovered that he even had Twitter accounts where he advertised his product.
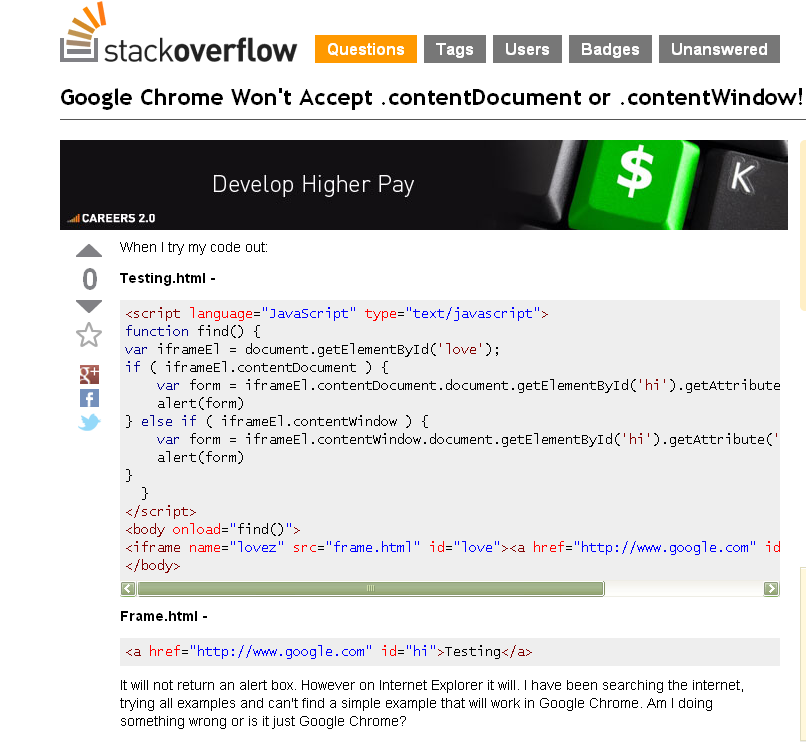
He also posted a question on the programming forum StackOverflow, asking for help with a piece of Javascript code.
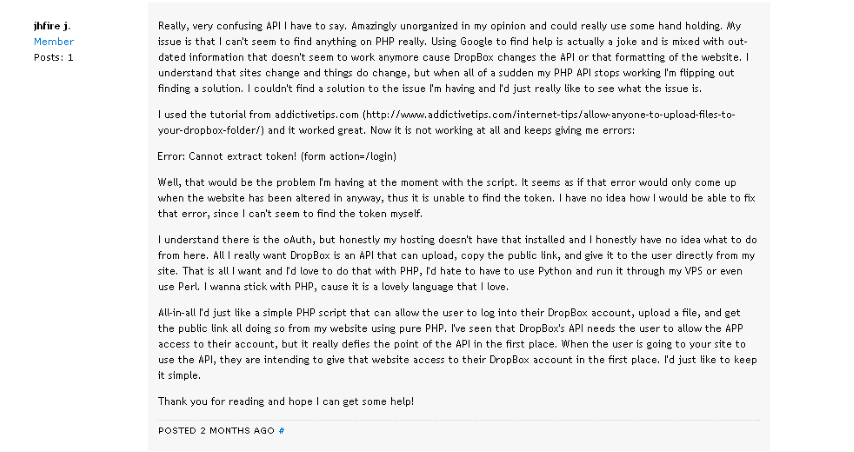
He also complained on the Dropbox forums about their application programming interface (API) which he used to download the malware executables onto victims' computers. I would like to point out that Dropbox was unaware of this abuse of their system and responded promptly and professionally when we notified them.
On Web of Trust, a service that allows users to classify websites as safe or dangerous, he even complained that his website had been flagged as malicious.
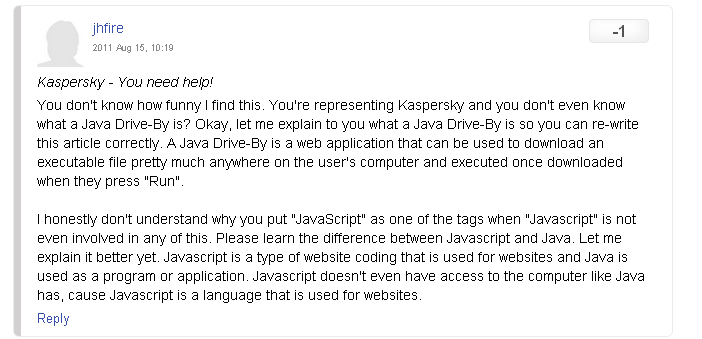
He also commented on an article in Kaspersky's blog complaining about their explanation of a drive-by download.
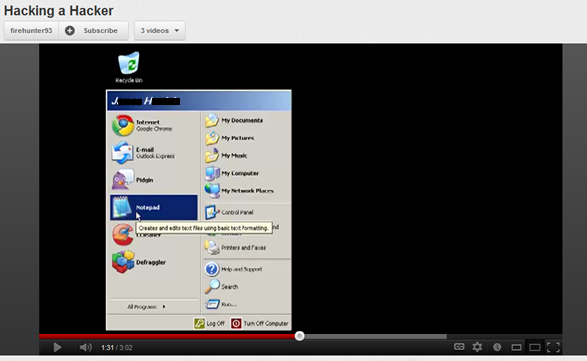
I also found a YouTube account. Amongst the videos he posted, there is one called Hacking a Hacker were you can see a name appear for a brief moment on the Windows Start menu. Oops.
Searching for one of the email addresses extracted from the WHOIS entries returns the same name on Skype.
Conclusion
While there is a humorous side to this case it illustrates a somewhat troubling trend which is the commoditization of malware services. Services such as automated packing, scanning to verify evasion of current antivirus signatures, preconfigured exploiting servers, renting of botnets for spam distribution or denial of service attacks; pretty much everything cybercriminals need can be paid for and used with a few clicks. And while most of those services are advertised in underground forums, the fact that we are seeing more and more of them with public websites posing as legitimate businesses is a cause for concern.
It is also difficult to get these services closed, even in evident cases of abuse like this one. We contacted the registrars and webhosts used by FoxxySoftware with limited success—the website is still accessible at the time of publication[1]. We strongly caution you against going there as it is a perfect target for malicious content.
[1] We want to thank Dropbox and PublicDomainRegistry for quickly taking action after we contacted them.