I want share with you what ESET Latin America’s Research team thinks will be the main trends in malware and cybercrime in 2012. In our office it is usual to produce an analysis of emerging trends in a year-end report and so, in keeping with recent postings by my ESET colleagues, I present a summary of the report we published a few days ago entitled (translated from Spanish, of course): “Trends for 2012: mobile malware”. Here is an extract from the introduction:
Users habits, the way they use technologies typically influence and determine malware development; that will continue in 2012. Accordingly, the significant growth in the use of mobile devices will be critical next year, given that these platforms are no longer off limits to malicious code. Malware developers have been working hard over the past few years to infect these devices and this report describes the way that desktop-computer threats have migrated into the mobile world and are becoming increasingly widespread.
Within this context, threats involving mobile devices (including, but not limited, to new malicious code, as well as Internet fraud schemes) will be the most pressing issue in 2012, in addition to the appearance of new types of attacks and variations of the existing ones. (Tendencias 2012: El malware a los móviles)
At the beginning of this document we made it clear that, in our opinion, mobile malware will be next year’s highlight: the creation of new threats and especially variations of existing ones. Today there are five billion mobile devices in the world, one out of four of which is a smartphone, that is, a mobile phone with the ability to connect to the Internet and to be used to access e-mails (personal or corporate), social networks and even eCommerce sites or Home Banking. In addition, the increased storage capacity of mobile devices makes them a target of high interest to hackers based on the amount of information potentially available on them.
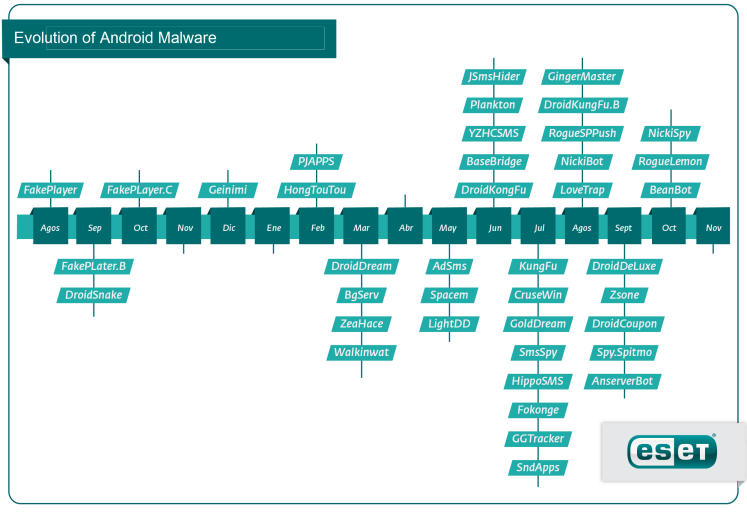
In this context, Android, Google's Operating System and market leader with 43% market share, will stand out in 2012 as it has been the focus of attention from malware developers for mobile devices for some time. The following chart shows the evolution of 41 malicious codes on this platform:
Note that the timeline begins in August 2010, with the emergence of FakePlayer, the first Trojan for Android, and continues until October this year when we finished editing this document. At that time, as already mentioned, we had identified 41 major malicious codes (and variations) for this platform. It is also important to note that the graph shows the density of occurrence, and that 65% of the threats were discovered in the past five months, highlighting the trend identified for next year. Also, other findings of this analysis indicate that:
- 30% of threats were made available for download in the Android Market.
- 37% are SMS Trojans.
- 60% of the malicious codes have some botnet characteristic, i.e. some kind of remote control over the device.
We also document two important findings regarding mobile threats in our report: The DroidDream incident, which is the first mobile malware with massive impact (250 thousand users affected) and an analysis of Android’s emerging role in terms of malware for mobile platforms (Is Android the new Windows XP for mobile malware?).
However, there are other predictions worth noting for 2012 beyond mobile malware:
1. According to statistics published by Gartner, Windows 7 will become the most widely used operating system in the world by the end of 2011, with 42% of the market share. This event, which will knock Windows XP from the first place, also implies some changes in threats developed by cybercriminals. The improvements in the security provided by the newer operating system involve the development of more technologically advanced malicious codes, with the purpose of evading these protection mechanisms. In conclusion, we foresee the evolution of complex technological threats aimed at infecting new operating systems like Windows 7 and Windows 8, and even running on 64 bit bypassing the enhanced security mechanisms that they possess.
2. Secondly, localized attacks will continue appearing, as we see in our Latin American Laboratory on a daily basis. Local attackers are accustomed to using regional incidents for Social Engineering purposes and to propagate different attacks. Just as ransomware is relatively common in Russia, here in Latin America we are accustomed to seeing phishing attacks and banking Trojans that steal home banking credentials from infected users.
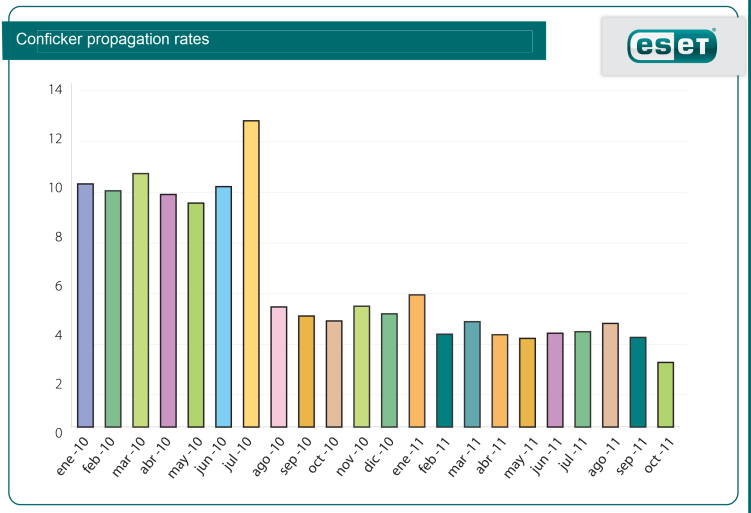
3. Another consequence of the migration from Windows XP to Windows 7 as the leading operating system is the possible disappearance of Conficker. This computer worm appeared in November 2009 and became one of the most important worms of the last few years, placing among the three most detected threats for 3 years, according to the monthly threat reports by ESET Latin America. Nevertheless, the trend of detection of this malicious code is decreasing, as shown by the ThreatSense.Net statistics, ESET's early warning system:
4. Finally, we will see more hacktivism, Internet attacks for ideological purposes rather than financial ones. We have seen a lot of attacks in Latin America in the last months (including attacks directed at government sites in Mexico, Brazil and Argentina) and it is logical to expect more of them, not only in our region, but in the rest of the world. Companies and organizations need to consider protection not only against traditional cybercrime, but also against groups like Anonymous and ideologically-motivated attacks.
Corporate and government entities will need to deploy a combination of effective technologies and best practices to fend off attacks and minimize data leakage, including staying informed about emerging threats. We will continue to provide not only security technology solutions but also helpful information through our different security awareness and education initiatives.
In conclusion, for some years now there has been relative stability in the world of malicious code: we saw worms and Trojans, distributed by email and social networks, infecting users, focused on information theft. Today, the mobile world and new digital platforms are generating a wider diversity of malicious codes. These new devices give rise to new patterns of user behavior, and new targets for attack, not only because they have a greater amount of sensitive information but also because these mobile devices one can be used to access systems that were previously accessible only through desktop computers. Information theft via smartphone today not only represents access to a contact list, but also access to confidential files, private images or even passwords for sensitive systems.
This opens the door to the rise of new attack vectors and modes, where mobile platforms have a greater significance, but at the same time not diminishing the threats to desktop computers. Users will have to be aware of the value of the information they transport in their mobile devices on a daily basisi and will have to understand that they not only can compromise their confidentiality while using web services but also by the loss or physical theft of the devices.
This does not necessarily represent a complete migration of malware to mobile devices, or the rise of a new era; however, it does imply important changes in the malware and cybercrime eco-system.
Sebastian Bortnik
Awareness & Research Coordinator
ESET Latin America