The Trojan downloader malware Win32/TrojanDownloader.Agent.QXN that showed up in my email about 10 days ago made a return visit today, posing as a pair of emails from the United States Postal Service. The first time the malware showed up it was dressed up, as a package delivery receipt from Canada Post. But this time the presentation was fairly unimaginative, as you can see here.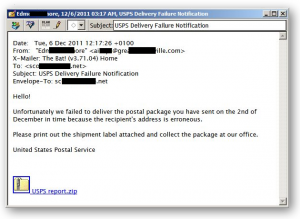
The message is in plain text from an email address that does not resemble a USPS address. The text is not full of typos but it lacks logic and it is, at least to my ears, strangely worded (can you recall any USPS documents that employ the phrase "the recipient's address is erroneous?").
Furthermore, the malware delivery mechanism here is fairly primitive. There is a zip file attached to the email and this contains an executable that the intended victim must therefore extract and run to get infected.
The faked Canada Post delivery mechanism was a plausible URL that triggered a file download. The Trojan itself was presented as a somewhat obscure file type with the extension .PIF, not the more obvious .EXE extension used in this case. The .PIF extension offers the added benefit of being easily confused with .PDF by novice users.
Of course, even an unsophisticated malware delivery system still means that some recipients of this email will execute the Trojan code and open up a back door on their systems, one that may lead to all their data and a whole lot more. Fortunately, this particular piece of malware is widely recognized by antimalware programs. In fact, it is unlikely to make it as far as your in-basket if you are using Gmail or a major ISP. Nevertheless, the fact that this showed up twice in one day in my in-basket serves as a reminder to be vigilant at this time of the year, a time when package delivery is on the minds of many.
If you want to educate friends and family about how this type of attack works, here is a short video I made using the Canada Post example. Feel free to share it:




