We realize there have been a lot of articles in the blog now about the Win32/Stuxnet malware and its new vector for spreading, but when vulnerabilities emerge that can be widely exploited, it is important to share information so that people can protect themselves from the threat.
Detection for Win32/Stuxnet and the shortcut (LNK) files used to spread it were initially added in virus signature database update 5282, which was released on Thursday, July 15, 2010. The shortcuts used to initially spread this malware are reported as LNK/Autostart.A trojan by ESET. On Tuesday, July 20, 2010, an additional form of heuristic detection was added for shortcuts containing the vulnerability, which are detected as LNK/Exploit.CVE-2010-2568. So, protection has been available for this threat for almost a week.
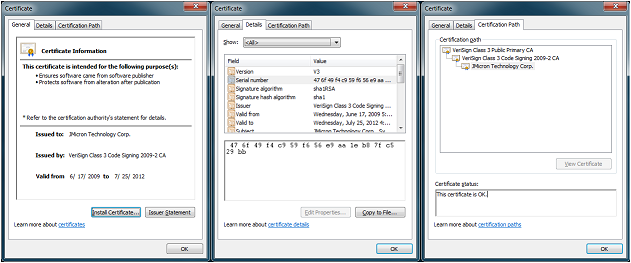
On Saturday, July 17, 2010, ESET Senior Researcher Pierre-Marc Bureau reported that a new device driver for the Win32/Stuxnet worm digitally signed with a code-signing certificate belonging to "JMicron Technology Corp.". At the time of the report, it was unclear whether this was a new certificate which had been fraudulently obtained or was a legitimate certificate that had been stolen. ESET's virus lab has since confirmed this digital certificate is the same one used by JMicron to sign device drivers in their JMB 36x Host Controller Drivers R1.17.55 package, which means the certificate was, in fact stolen. A screen shot of the certificate from this package:
The serial number for this digital certificate is "47 6f 49 f4 c9 59 f6 56 e9 aa 1e b8 7f c5 29 bb." VeriSign reports here in their blog that they have revoked both this digital certificate and the earlier one used by RealTek to prevent further misuse by malware authors.
We have received several questions about the number of Win32/Stuxnet infection attempts, as reported to us by customers through ThreatSense.NET, ESET's telemetry system. To date, that number remains miniscule, accounting for just a few hundredths of a percent of the types of malware we receive reports about on a daily basis. Those infections, though, have an unusual geographic spread. At the time of this writing the top countries are: the United States, Iran, Russia, Indonesia and the Faroe Islands*, with the rest of the world accounting for the remaining of infections. Please note that geographic data like this from our virus lab can change in just a few minutes, which is why the country list may appear slightly different than previous reports.
Aryeh Goretsky, MVP, ZCSE
Distinguished Researcher
*We were surprised by the number of reports received from the Faroe Islands and thought this might be an error. It was verified, and a special thanks to David Harley for his investigation into the economy of the Faroes.